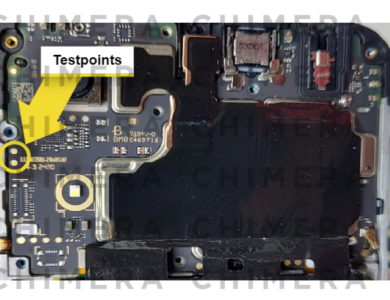
TestPoint
Vivo Y19 Pattern/FRP New Security Testpoint Method
This article will explain this feature of the Vivo Y19 test point/EDL Point. Edl Point is also known as Emergency Download Mode. It can be utilized to open the bootloader on the phone. When your device is locked, unlock your phone’s bootloader, but it is not unlockable, and in this case, you must take your phone into EDL Mode.
If your phone runs on a Qualcomm processor, it will undoubtedly be able to support EDL Mode, also known as Emergency Download Mode. But not all Qualcomm processors can support this. But, at present, The Meditech Processor Phone is also being utilized for unlocking the bootloader.
ERASE FRP BY
=====================================
How To Boot : Power off phone
* BROM : Turn Off Phone, Hold VOL + And VOL- Then Insert Cable
* Preloader : Just Insert cable!
=====================================
Waiting For Device Connection…. OK
Initializing usb… OK
Reading Hardware Information… OK
Chipset : MT6768(Helio P65/G85 k68v1)
HW : 0x0
WDT: 0x10007000 Uart: 0x11002000
Brom Addr : 0x100a00 DA Addr : 0x201000 CQDMA Addr: 0x10212000
Var1: 0x25
HW code : 0x707
Security Config… OK
SBC: True SLA: False DAA: True SWJTAG: True
Mem read auth: True Mem write auth: True
MEID: 88BBA3FFD6AB49C7BDB58D4FEA74E65D
Loading payload: mt6768_payload.bin, 0x264 bytes
Sending payload… OK
OK
=====================================
How To Boot : Power off phone
* BROM : Turn Off Phone, Hold VOL + And VOL- Then Insert Cable
* Preloader : Just Insert cable!
=====================================
Waiting For Device Connection…. OK
Initializing usb… OK
Reading Hardware Information… OK
Chipset : MT6768(Helio P65/G85 k68v1)
HW : 0x0
WDT: 0x10007000 Uart: 0x11002000
Brom Addr : 0x100a00 DA Addr : 0x201000 CQDMA Addr: 0x10212000
Var1: 0x25
HW code : 0x707
Security Config… OK
SBC: True SLA: False DAA: True SWJTAG: True
Mem read auth: True Mem write auth: True
MEID: 88BBA3FFD6AB49C7BDB58D4FEA74E65D
Loading payload: mt6768_payload.bin, 0x264 bytes
Sending payload… OK
OK
**** New Brom Exploit ****
Tips : Please Don’t Remove battery and usb cable!
Process may take 1 to 2 Minutes ( Please Wait )
Analyzing… preloader_-8DAXFlash – Uploading xflash stage 1 from MTK_AllInOne_DA_5.2136.bin… OK
preloader to Jumping… OK
DRAM config needed for : 150100445636444d
Sending EMI data… OK
Reading Storage Information… OK
EMMC ID : DV6DMB
EMMC CID : 150100445636444d4202cc2c685f17e3
Boot1 : 4 MB Boot2 : 4 MB RPMB : 16 MB
Userarea : 116.48 GB
Erasing FRP… OK
Process may take 1 to 2 Minutes ( Please Wait )
Analyzing… preloader_-8DAXFlash – Uploading xflash stage 1 from MTK_AllInOne_DA_5.2136.bin… OK
preloader to Jumping… OK
DRAM config needed for : 150100445636444d
Sending EMI data… OK
Reading Storage Information… OK
EMMC ID : DV6DMB
EMMC CID : 150100445636444d4202cc2c685f17e3
Boot1 : 4 MB Boot2 : 4 MB RPMB : 16 MB
Userarea : 116.48 GB
Erasing FRP… OK